CADE Shields You Against CVEs and Mass Exploitation
Staying Ahead of Emerging Threats
In today’s hyper-connected digital battleground, it isn’t just the elusive zero-day that demands your attention—it’s the relentless onslaught that follows every disclosed CVE. Once a vulnerability is stamped with a CVE number and its details hit the public domain, cybercriminals mobilize instantly, weaponizing exploits in a brutal race against time. This is where our next-gen Web Application Firewall (CADE (Web Application Firewall – WAF Module)) steps in: not with half-measures, but with the full force of automated, AI-driven intelligence that preempts the chaos of mass exploitation.
From Vulnerability to Attack
Traditional defenses can’t keep pace with the rapid evolution of threat tactics. Right out of the disclosure gate, attackers are hunting for vulnerabilities like CVE-2025-24813—a critical flaw that lets them hijack your trusted systems. In the blink of an eye, automated scripts and botnets are scanning the globe, targeting unpatched systems while outdated protection schemes scramble to catch up. This isn’t about defending yesterday’s threats; it’s about anticipating tomorrow’s onslaught.
The Limitations of Legacy Defenses
Conventional CADE (Web Application Firewall – WAF Module)s are stuck in a bygone era—relying solely on static rules and signature-based detection that simply can’t contend with fluid, client-side attacks. They miss the intricate details of how attackers break apart their payloads, reassemble them right at the final mile, and slip past network-bound filters. Like leaving the front door wide open, such outdated paradigms enable sophisticated threat vectors, from file chunking to encrypted payload smuggling.
From Vulnerability to Attack
Our solution shatters the limitations of legacy defenses by merging rule-based fortifications with advanced AI capabilities. It’s designed to do the heavy lifting for you:
- Real-Time Vigilance & Automated Rule Deployment: As soon as a CVE—whether it’s the critical CVE-2024-55956 or any emerging threat—hits the streets, our CADE (Web Application Firewall – WAF Module)’s threat-hunting engine springs into action. It continuously scans CVE databases and exploit forums, enabling it to generate and deploy custom defense rules faster than the competition can blink.
- Layered, Adaptive Defense: Even when attackers tweak their techniques on the fly, our CADE (Web Application Firewall – WAF Module)’s powerful AI/ML engine reinterprets anomalous traffic patterns and reassembles threat landscapes in real time. This layered approach means that every stage of an attack—from initial discovery to mass exploitation—is intercepted before it can take hold.
Before diving into the staged sequence of events, consider this: the moment a vulnerability becomes public, the race against time begins—every second counts in turning a disclosed flaw into a full-blown attack.
- Disclosure: A vulnerability is identified and assigned a CVE (e.g., CVE-2025-24813), with details that are released publicly.
- Weaponization: Attackers reverse-engineer patches or develop exploit scripts, often within hours because the faster one hits the better it is chance to exploit before someone else..
- Mass Exploitation: Automated bots scan and attack vulnerable systems globally. Research indicates that 76% of exploits emerge within seven days of disclosure, underscoring the urgency of timely defenses.
Time Is of the Essence
History has shown us that delayed action is fatal. With exploits like Log4Shell and ProxyShell still wreaking havoc long after their initial disclosure, the stakes couldn’t be higher. Our CADE (Web Application Firewall – WAF Module) isn’t just about keeping up; it’s about outpacing an adversary who never stops evolving. It’s built for scenarios where every second counts, ensuring that your applications are shielded from CVE-driven attacks the moment they emerge.
Legacy CADE (Web Application Firewall – WAF Module)s, reliant on manual updates, often fail to keep pace. Our solution bridges this gap with real-time protections to stay prepared to fight against this threats.
Real World Example
CVE-2025-24813
Vendor: Apache Tomcat
CVSS Score: 9.8 (Critical)
Description: A path equivalence flaw in Apache Tomcat’s Default Servlet enables remote code execution via manipulated file names.
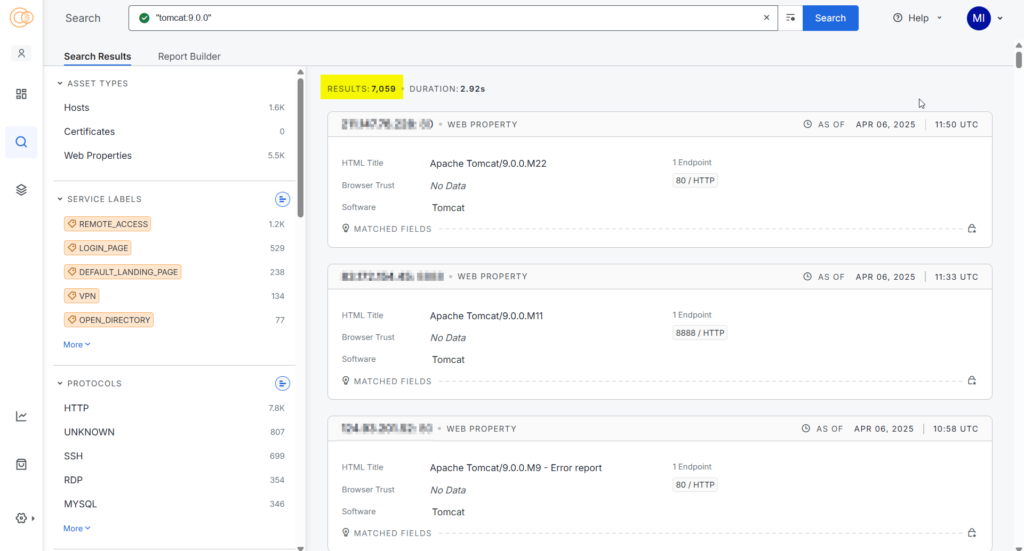
A quick search on Censys shows a large number of web properties that are affected with the vulnerability, these are exploitable with this vulnerability under certain conditions. So can you imagine the scenario? Still, horrible.
Exploitation: Under specific conditions, attackers can execute arbitrary code on vulnerable servers without authentication.
In our CADE, we have created our shield to protect against these vulnerabilities. To keep you protected from these mass attacks when a new vulnerability comes out.
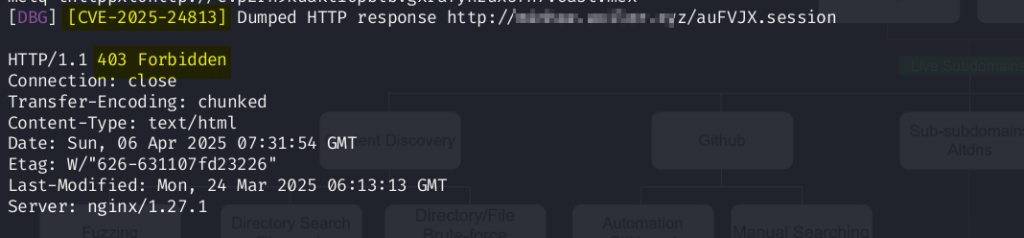
As shown above, our CADE (Web Application Firewall – WAF Module) will block those attacks and keep you safe.
CVE-2024-55956
Vendor: Cleo (Managed File Transfer)
CVSS: 9.8 (Critical)Description: An arbitrary file upload flaw in Cleo’s MFT software (Harmony, VLTrader). Exploited by Cl0P ransomware for data theft and extortion campaigns.
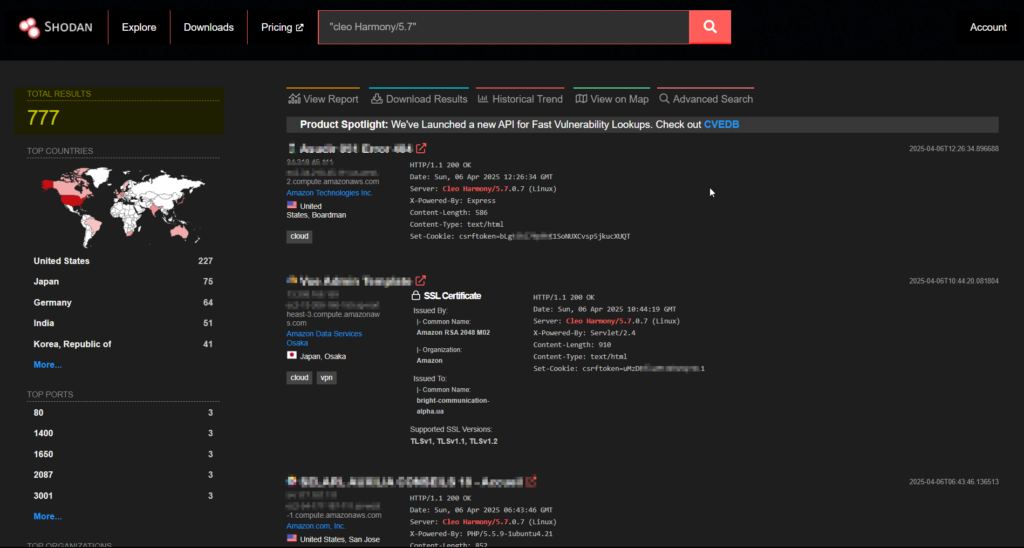
As shown above, a portion of vulnerable technologies with this CVE, that can be exploited still now. There are many more to get discovered with other search parameters. They are still indifferent and thousands like this still even after so many days passed by and the attackers are exploiting them day after day.
Exploitation: Affected high-profile targets like Blue Yonder, leading to data leaks.
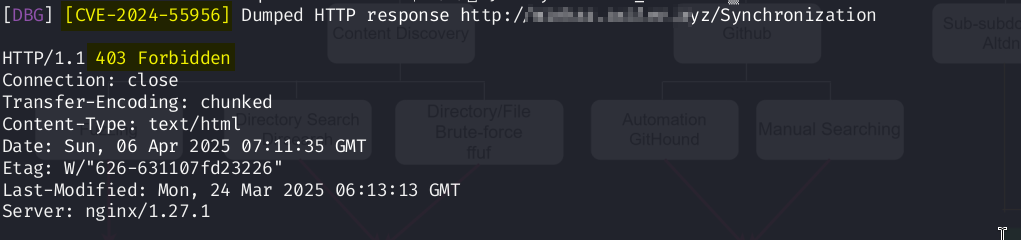
Here you go, our CADE blocks these exploiting requests to keep you protected against these CVE attacks that are deadly as the attackers launch attacks in large scales.
How Our CADE (Web Application Firewall – WAF Module) Stays Ahead of the Curve
1. Real-Time CVE Monitoring & Threat Intelligence
Our security team and automated systems monitor CVE databases (NVD, MITRE), exploit forums, and dark web channels on a regular basis. When a new CVE is published, we:
- Analyze its impact on web applications for validation.
- Map the vulnerability to potential attack patterns.
2. Automated Rule Deployment
Within a short period of a CVE’s public release, our CADE (Web Application Firewall – WAF Module) generates and deploys custom rules to block these exploit attempts. For example:
- CVE-2024-21887: A command injection vulnerability chained with CVE-2024-21887 (authentication bypass) to compromise VPN devices. We released a virtual patch to block malicious payloads targeting this flaw before most vendors issued updates.
3. Layered Defense Against Evolving Tactics
Even after blocking known exploits, attackers often tweak payloads. Our CADE (Web Application Firewall – WAF Module) combines rules based protection system along with our highly powered AI/ML detection system to keep you protected against all the odds.
The Cost of Delayed Action
Unpatched systems remain prime targets long after vulnerabilities are disclosed. Consider:
Log4Shell (CVE-2021-44228): Years after its discovery, attackers still exploit lingering unpatched instances.
ProxyShell (CVE-2021-34473): Over 100,000 servers were compromised due to slow patching.
Our CADE (Web Application Firewall – WAF Module) is quickly armed with the defensive ruleset to block these exploits from exploiting the application as soon as the CVEs are published.
